The cyber threat to Australian businesses is one of the most underestimated risks facing the industry. If a business is connected to the Internet, it is exposed to the threat of cyber events. Businesses risk facing financial losses, damage to reputation, loss of intellectual property and disruption to business activities.
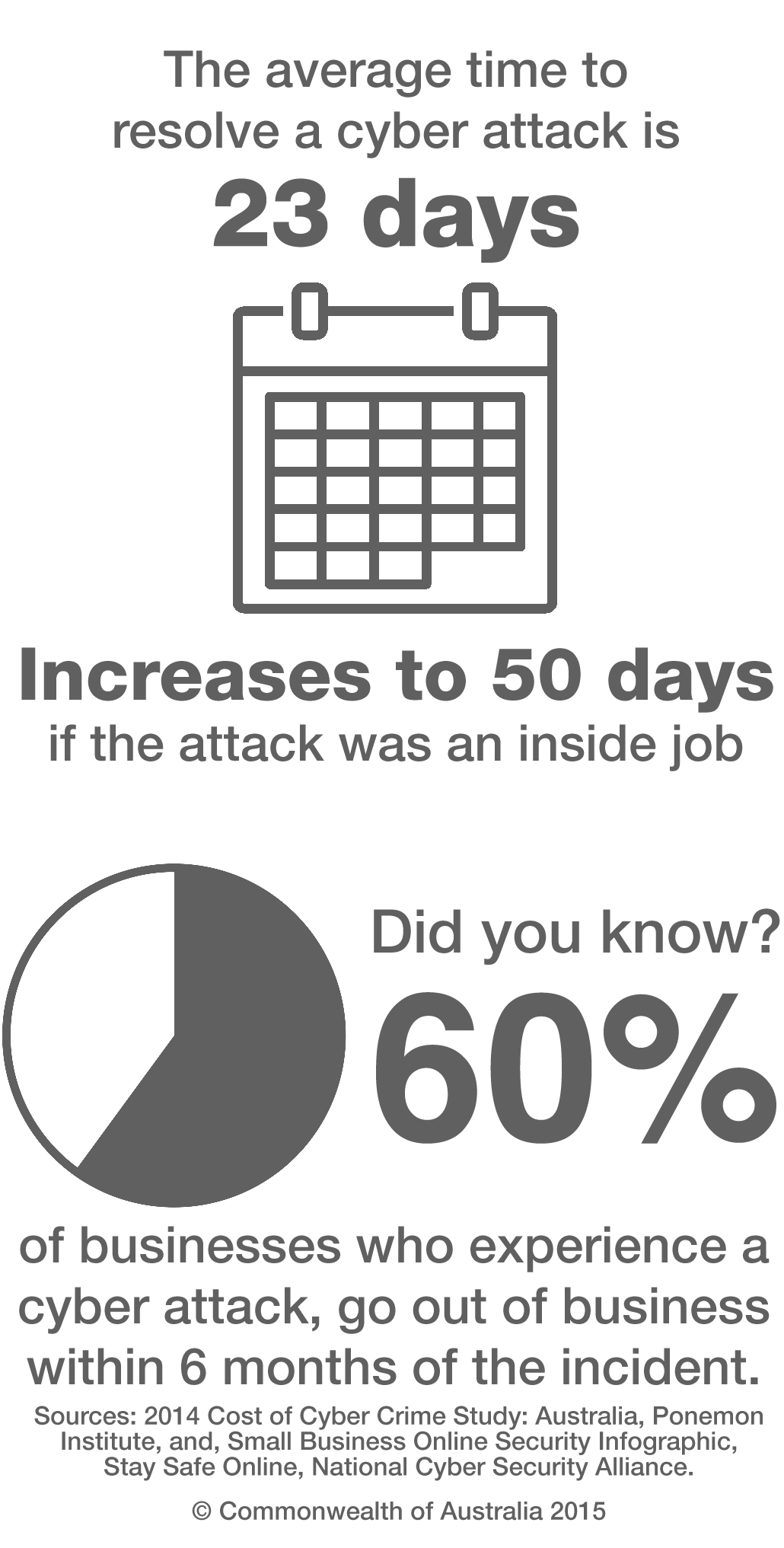
Ponemon Institute’s 2014 Cost of Cyber Crime Study found that the average time to resolve a cyber attack was 23 days, this increases to 50 days if the attack was an inside job. This resulted in 60% of businesses who experienced a cyber attack going out of business within 6 months of the incident.
Our Cyber Event Insurance policy comes with a 24/7 expert response service to minimise loss in the instance of a cyber event and aim to get your business back on track as soon as possible.
What constitutes a Cyber Event?

Point of Sale (POS) intrusions
Where retail transactions are conducted, specifically where credit card purchases are made. 85% of POS intrusions take weeks to be discovered.
High Exposure Industries
• Retail Sector
• Food Services
• Accommodation

Cyber Extortion
Crime involving an attack or threat against your IT infrastructure, couple with demand for money to stop the attack.
High Exposure Industries
• Professional services
• Administration
• Public Sector

Miscellaneous Errors
People make mistakes, some of which can compromise security. Including accidently posting private data to a public site, sending information to the wrong recipient or failing to dispose of documents securely.
High Exposure Industries
• Public Sector
• Administration
• Healthcare & Education

Cyber Espionage
Unauthorised network or system access linked to state affiliated attackers breach an organisation.
High Exposure Industries
• Professional Services
• Manufacturing
• Government & Military

Denial of Service
Attackers use ‘botnets’ of PCs and powerful servers to overwhelm an organisation’s systems and applications with malicious traffic, causing normal business operations to grind to a halt. Intended to compromise the availability of networks and systems.
High Exposure Industries
• Online Retailers
• Finance
• Public Sector

Physical Theft & Loss
The loss or theft of laptops, USB drives or printed papers, mostly from offices but also from vehicles and homes. 43% of theft/loss happened at work.
High Exposure Industries
• Healthcare
• Mining
• Public Sector

Insider & Privilege Misuse
Any unapproved or malicious use of an organisation’s resources. Due to the human nature of this event, even the best Anti Virus protection cannot stop this event.
High Exposure Industries
• Real Estate
• Public Sector
• Financial Institutions

Web App Attacks
When attackers use stolen credentials or exploit vulnerabilities in web applications such as content management systems or e-commerce platforms.
High Exposure Industries
• Information
• Utilities
• Retail

Payment Card Skimmers
Where a skimming device is physically implanted on an asset such as an ATM or POS terminal, to read your card data as you pay.
High Exposure Industries
• Retail
• Hospitality
• Finance

Crimeware
Is a broad category covering any use of malware to compromise systems such as servers and desktop. The primary goal is to gain control of systems to steal credentials.
High Exposure Industries
• Public Sector
• Information
• Utilities
Online Forms
Reference Documents
Small Business Guide: Protect Your Business
Stay Smart Online Alert Service

Data Breaches occur every day
While hacking incidents are the most recognisable and expensive cause of data loss, they are not the most common. It’s a startling fact – simple human error accounts for almost one in three incidents.
The root causes of data breaches in Australia
Malicious or Criminal cyber attacks
Human Error including employee/contractor negligence and lost laptops
System Glitches that expose private files
Source: 2015 Cost of Data Breach Study: Australia Ponemon Institute
No matter the sophistication of the security system, there is little that can be done to eliminate the risk of human error. A common, accidental breach is a real business risk worth considering today.
Click here to fill out a Cyber Insurance Questionnaire
Insurance is just one way of protecting your business from cyber events, however there are a range of defence mechanisms can be applied to lessen the chances of having a cyber event. This is where our partnership with the Australian Cyber Security Centre (ACSC) comes in.
CRM Brokers are proud partners of the Australian Cyber Security Centre (ACSC) . The ACSC leads the Australian Government’s efforts to improve cyber security. Our role is to help make Australia the most secure place to connect online. They provide advice and information about how to protect yourself and your business online. When there is a cyber security incident, we provide clear and timely advice to individuals, businesses and critical infrastructure operators.
The ACSC have developer a Small Buinsess Cyber Security Guide to help small businesses protect themselves from the most common cyber security incidents. The Guide can be downloaded here and will provide you with the basics on how to protect the information entrusted to you by your customers and suppliers.
The ACSC Alert Service provides easy to understand online security information and solutions to help protect internet users at home, at work and on mobile devices.
Sign up to the Alert Service
For more information
Small Business Guide: Protecting your business in 5 minutes
Stay Smart Online have developed this guide, to help you put in place some basic online security practices. The Guide can be downloaded here and will provide you with the basics on how to protect the information entrusted to you by your customers and suppliers.
Cyber Risks on Directors and Officers
To find out more about Cyber Risks on Directors and Officers, click on the brochure. The article focuses on some of the potential implications for company directors around Cyber Crime and data breaches and provide a risk management checklist for both boards and directors. This publication was co-authored by DLA Piper Solicitors, Nitesh Patel and Ewen Hollingsworth.